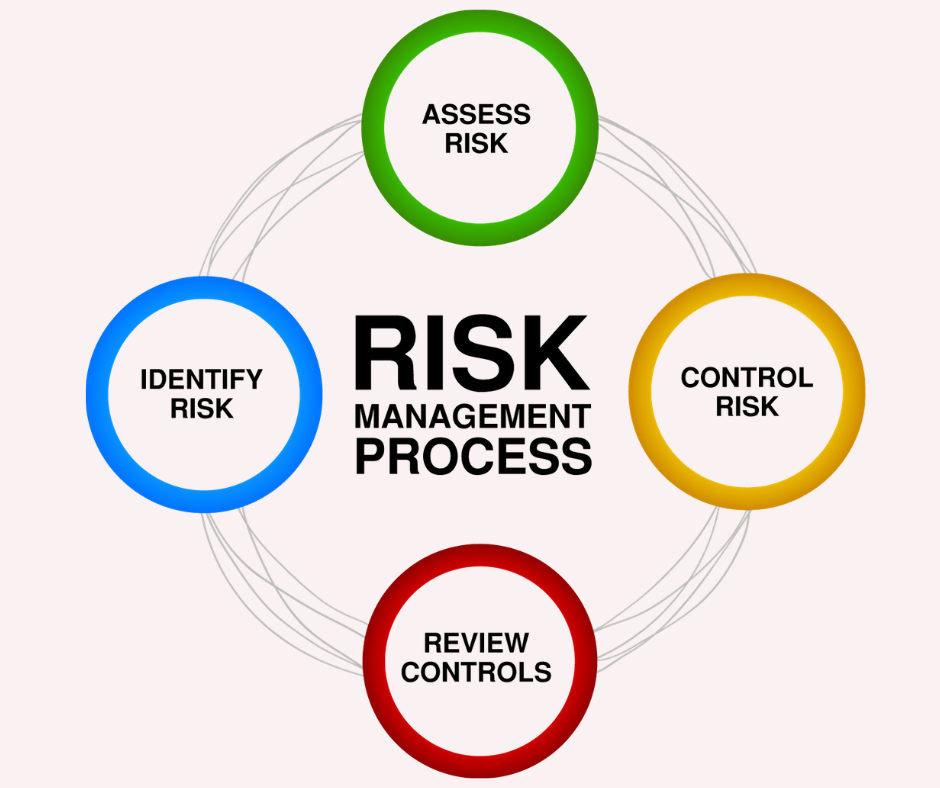
IT Risk Management is a crucial aspect of any organization’s operations. It involves identifying, assessing, and managing risks affecting an organization’s information systems and processes. Most IT risks can come in various forms, including cyber-attacks, hardware or software failure, data breaches, and natural disasters.
In today’s evolving threat landscape, securing the IT infrastructure is paramount for risk managers in any organization. As organizations continue to explore and invest in new technologies, detecting and managing the risk associated with newly deployed applications or systems is crucial.
Implementing the best IT risk management strategies is essential to minimize the impact of such risks and protect an organization’s reputation, customers, and assets. Managing IT risks is also crucial because a vulnerability can decrease trust and damage an organization’s reputation.
For example, the unresponsiveness of customer-facing applications for an hour due to scheduled maintenance or a cyberattack can lead to poor customer experiences and bad publicity. This article will discuss the best IT risk management strategies and how to apply them to safeguard your organization’s IT infrastructure.
Understanding The Activities In A Strategic IT Risk Management Plan
Before discussing risk management and its importance, let’s first understand the IT risk equation: Threat x Vulnerability x Asset = Risk. The logical equation highlights the relationship between different components constituting IT risk. It can also help in practical risk assessment. For example, assume your organization has weak security perimeters.
Or rather, let’s say your business has poorly configured network devices. In this situation, the vulnerability lies in your network devices or assets, which an attacker could exploit, a potential threat, to launch a cyberattack. The risk would be high since the network is highly vulnerable and the assets are critical.
In contrast, the risk would be medium if you have correctly configured devices with solid perimeter defenses. Risk assessment facilitates identifying, classifying, prioritizing, and mitigating various information technology threats. It can help organizations examine whether their security controls are adequate to tackle the consequences of potential threats or vulnerabilities in their IT infrastructure.
With clarity on components of IT risk, let’s discuss the importance of information security and risk management in any modern business or organization’s operations. Be that as it may, consider the four core constructs for your business’s robust and strategic IT risk management and assessment.
Including:
- Threat: This is any event, action, or incident with the potential to compromise system security. It can be intentional and accidental, including malware, equipment failure, human error, and natural disasters.
- Vulnerability: This aspect denotes the shortcomings or gaps in the information assets attackers can exploit to steal sensitive information. Identifying information system weak points and their exploitation methods is critical to mitigating overall IT risk.
- Asset: This is a broad term referring to an organization’s software, hardware, stored data, IT security policies, privileged users, and even file folders containing sensitive data.
- Cost: This is an organization’s overall harm due to a security incident. It can be monetary, reputational, or both. When determining the IT risk, consider the overall adverse impact if the data is compromised or stolen.
Articulating a well-defined risk management strategy and putting it into action can help organizations mitigate IT disasters. It also serves as a blueprint for IT teams to establish the proper technical controls, such as firewalls and multi-factor authentication, to improve their organization’s security postures.
Likewise, the involvement of senior executives is vital to channel the IT security risk management efforts in the right direction. With early detection of risks, you can minimize unexpected network downtimes to improve overall customer satisfaction. IT risk prevention also helps you prove compliance with various data security mandates and industry regulations, such as GDPR.
A robust, transparent IT risk management and security assessment methodology is critical before initiating risk evaluation. One thing is sure: You can customize it based on your business’s legal, regulatory, and contractual requirements. With that in mind, outlined below are the essential activities of a modern business’s strategic IT risk management and security assessment process.
A. Identify valuable assets
First, compile a list of all the business-critical assets you’ll investigate for potential vulnerabilities. Examining an organization’s hardware, software, and information flows isn’t practically feasible. Therefore, you should prioritize and classify assets based on predefined standards like legal stature and business importance. Furthermore, you should incorporate these classification standards in your information risk management policy to save valuable time during the assessment.
B. Assess threats and vulnerabilities
Determine the threats and vulnerabilities capable of compromising your information assets’ availability, integrity, and confidentiality. Common IT-related hazards include malicious internal actors and natural disasters. Simultaneously, investigate vulnerabilities like old equipment, incorrect configurations, and unpatched systems in your organization, as attackers can infiltrate a network by exploiting these vulnerabilities.
C. Evaluate and prioritize risks
At this stage, compare, prioritize, and rank risks by determining their possible occurrence and subsequent impact on your information systems. Classify risks as high, medium, or low based on their assigned scores. Additionally, employ automated cybersecurity risk assessment and management tools for accurate risk analysis and identifying security events requiring immediate attention.
D. Mitigate or prevent risks
Next, after prioritizing risks, you can address them using the most suitable methods according to your business needs.
Including Risk:
- Avoidance is the most straightforward approach and requires organizations to evade activities potentially posing legal, financial, reputational, and operational risks. For example, you can avoid the risk of regulatory penalties by adhering to all the data security regulations in your region.
- Modification allows organizations to lessen the adverse impact of unavoidable risks by establishing robust physical, technical, and operational controls. Physical controls like biometric security scanners can help organizations protect their tangible assets. Similarly, technical controls involve utilizing antivirus software, firewalls, and access management tools to prevent security incidents. Lastly, operational controls comprise robust security policies and procedures for smooth business functioning.
- Transfer enables organizations to mitigate the consequences of risk by transferring or sharing it with a third party. Cloud vendors, for example, reduce the risk of business interruption for their clients by providing off-site data backups.
- Acceptance says eradicating or transferring every risk is practically impossible, so an organization must accept specific threats as part of its overall security risk management process. For example, organizational networks have inherent risks—such as unexpected outages—but businesses still rely on them for communication or information exchange.
E. Document, audit, and review
Lastly, prepare a detailed risk assessment report for auditing and compliance purposes. These reports should outline all the possible threats and associated risks, vulnerabilities, and possibilities of occurrence. Risk control measures and their implementation procedures should also be a part of the report. These control measures should be suggested based on the risk level. Continuously review and update these reports to improve the effectiveness of your IT risk management framework.
The Most Common IT Risk Management Strategies In Modern Business
As mentioned, IT risk management identifies, assesses, and manages IT risks. The process involves analyzing potential risks, evaluating the likelihood and impact of those risks, and developing and implementing strategies to mitigate or manage the risks. The ultimate goal of IT risk management is to minimize the impact of potential risks on an organization’s operations and protect its assets, reputation, and customers.
In other words, IT Risk Management involves policies, procedures, and tools to identify and assess potential threats and vulnerabilities in IT infrastructure. Usually, the IT risk management process denotes the probability of an unexpected, adverse business outcome when a specific threat or malicious actor exploits an information system vulnerability. It could range from human error and equipment failure to cyberattacks and natural disasters.
Therefore, IT Risk Management is the application of risk management methods to manage IT threats. At all costs, IT Risk Management involves procedures, policies, and tools to identify and assess potential threats and vulnerabilities in IT infrastructure. There are several IT risk management strategies that organizations can use to mitigate IT risks. These strategies include:
(i). Risk Assessment
Risk assessment is the first step in IT risk management. It involves identifying potential risks that can affect an organization’s IT infrastructure. A risk assessment should be conducted periodically to identify and address new risks. A thorough risk assessment will help organizations prioritize and allocate resources to mitigate the most critical risks.
(ii). IT Risk Mitigation
Risk mitigation involves developing and implementing strategies to reduce the likelihood and impact of potential risks. The strategy may include implementing security controls, conducting regular vulnerability assessments and penetration testing, and ensuring that software and hardware are updated regularly.
(iii). Recovery And Continuity
Disaster recovery and business continuity planning involve developing strategies to ensure that critical IT systems and processes can be restored quickly during a disaster. The strategy may include developing backup and recovery plans, implementing redundant systems, and conducting regular disaster recovery testing.
(iv). Training And Awareness
Training and awareness programs are essential in mitigating IT risks. Organizations should conduct regular training sessions to ensure that employees know the potential risks and understand how to identify and report any suspicious activity. The training should cover phishing scams, password management, and safe browsing practices.
(v). Incident Response
Incident response involves developing and implementing strategies to respond to security incidents quickly. The methods include developing incident response plans, establishing an incident response team, and conducting regular training and testing.
The Practical Methods To Include In A Strategic IT Risk Management Plan
Effective risk management begins with discovering and assessing all potential vulnerabilities in an IT environment, such as weak system passwords, unpatched systems, and malicious software downloads. However, manual identification and assessment can be costly and resource-intensive.
Instead, organizations should leverage automated tools—such as help desk or service desk software—offering risk management capabilities. Such tools automatically identify and assess risks and alert security teams about potential issues. Technically, a CMDB is a crucial part of the ITIL framework. It enables organizations to manage, control, and configure assets.
Remember, ITIL is a set of best practice guidelines focused on aligning the delivery of IT services with business goals. At the same time, file-sharing security is all about utilizing suitable file security tools, transfer protocols, and procedures while exchanging sensitive business documents inside or outside the company network.
On the one hand, to create a working IT Risk Management plan, try to patch management software designed to address software vulnerabilities quickly. On the other hand, to apply IT risk management strategies effectively, organizations should follow some of the best techniques and practical methods. They’ll act as the guideline for an effective plan implementation.
1. Ensure transparent and clear communication
Formulating robust internal and external communication strategies is crucial to conveying risk details to concerned parties. Clear communication facilitates a faster, coordinated response against threats in your IT environment. It can also assist in speedier risk mitigation, assessment, and monitoring. Take input from all critical stakeholders while forming your risk communication and management strategy to understand all the aspects of a given risk, including parties affected, significant challenges, and potential recovery costs.
2. Continually perform IT asset management
Monitoring IT assets such as routers and servers can help you minimize technology risks. You can employ reliable asset life cycle management software to run and maintain an automated, centralized network inventory, providing detailed insights into your assets’ performance, security, and licensing issues. For example, you can continuously monitor and track software license expiration dates and receive automated alerts with IT asset management solutions.
3. Establish Clear Roles and Responsibilities
Implementing effective IT risk management strategies is essential for organizations of all sizes and industries. It helps to ensure the safety of their data and systems, and it can also help them avoid costly security breaches or system downtime. To apply IT risk management strategies effectively, organizations should try to manage and audit user access rights across their IT infrastructure.
4. Identify and assess potential risks
The first step in implementing an IT risk management strategy is identifying and evaluating potential risks. This involves understanding the organization’s assets, systems, and processes and identifying any vulnerabilities or potential threats. In this case, Active Directory (AD) groups help keep a tab on the access permissions to various resources in your network, such as computers.
5. Develop strategies to address risks
Realistically, there are various forms of IT risk management needs in any modern business such as email spoofing. Email spoofing is a cyberattack that tricks users by sending malicious emails from forged users or trusted accounts. Once potential risks have been identified, organizations must develop strategies to manage them. This might involve implementing new security protocols, updating software or hardware, or creating a disaster recovery plan.
6. Monitor and update the plan
IT risk management is ongoing; continuously monitoring and updating the plan is essential. This ensures that the organization’s risk management strategies remain practical and up-to-date. For instance, as defined in the IT infrastructure library, the IT service catalog is an organized repository of an organization’s active IT services that end users can request and use efficiently. It falls under the IT service portfolio, which provides more in-depth insights into a company’s IT services, including active and retired services and products and products currently in the production pipeline.
7. Disaster recovery and business continuity
By all means, all modern businesses need to improve their security posture and quickly demonstrate compliance with an easy-to-use, affordable SIEM tool. This includes integrating a modern IT service management (ITSM) solution to eliminate barriers to employee support services. Equally important, disaster recovery and business continuity plans are critical components of IT risk management. It’s essential to test these plans regularly to ensure they are practical and can be implemented quickly and efficiently during a disaster.
8. Strengthen your cybersecurity infrastructure
Building and maintaining a secure IT infrastructure is critical to preventing cybersecurity risks. It would help to employ the right security tools, policies, and procedures to impede various threats. Aside from firewalls and antivirus software, utilize next-gen security tools such as security information and event management (SIEM) to enhance your security controls. Automated tools like SIEM software maintain a detailed log of security events and correlate data to identify threats quickly. Furthermore, they allow you to set automatic responses against security incidents, such as blocking IP addresses associated with unauthorized activities. Likewise, you can leverage built-in templates to generate security and compliance reports.
9. Implement a seamless data access control
Establishing strict authentication and authorization procedures can minimize the data security risks in your organization. Modern access management software can help ensure that only authorized users have access to the most sensitive parts of your network, reducing the risk of insider threats. Furthermore, such tools continuously monitor the changes in your file system to track unauthorized alterations. They also help generate compliance reports outlining user permissions and activities. With tools like these, you can proactively follow privileged users’ accounts for unusual activities to stay better prepared against advanced threats.
10. Train your IT risk management employees
Employees are often the weakest link in an organization’s security, so it’s crucial to provide regular training to help them understand the importance of IT security and how to avoid potential risks. Notwithstanding, by following these and other related resource steps, organizations can implement effective IT risk management strategies and help to protect themselves from potential threats. However, it’s important to note that no plan is foolproof, and organizations should always be prepared to respond quickly and effectively to any security breaches or system downtime.
Summary Notes:
In conclusion, implementing effective IT risk management strategies is crucial for organizations to mitigate potential risks and ensure the safety of their data and systems. Identifying and assessing potential risks, developing strategies to address them, and continuously monitoring and updating the plan is essential.
This guide has provided valuable insights into the best IT risk management strategies and how to apply them effectively. By following these strategies and best practices, organizations can better protect themselves from potential threats and ensure the continuity of their business operations in the face of a disaster.
Testing disaster recovery and business continuity plans is also critical to ensure their effectiveness. By testing these plans, organizations can identify weaknesses and modify them before a disaster strikes. We hope this guide has given you the knowledge and tools to implement your organization’s best IT risk management strategies.
Eventually, by following the guidelines mentioned above and continuously monitoring and updating your plan, you can better protect your organization from potential risks and ensure the safety of your data and systems. Furthermore, if you need more help, you can always consult our Webtechex Team for more support.