Ready or not, Industry 5.0 is here. While many manufacturers are still busy developing methods for interconnecting new technologies to improve efficiency and productivity — the guiding principle behind Industry 4.0 — the next phase of industrialization is already upon us. But Industry 5.0 is not akin to Spinal Tap’s Nigel Tufnel explaining that his guitar amplifier is louder.
More so than standard models because “this one goes to 11.” It’s much more than simply bumping up industrialization one tick higher on the dial. It’s the next step in the evolution of manufacturing. Recently, some researchers have focused on specific lasting “affordances” of documentary material over digital documents. It’s often assumed that there’s a link between the two media.
Although there is stiff competition, this is a complementary relationship. During a dynamic (changing in time) digital documents as well as the intangible (made from information material) and the agency (able to initiate deeds), newsprint records are everlasting when published. When “Frozen” offers a permanent record of a historical record condition, it can be lost but cannot be changed.
Still, it’s portable: small, autonomously transportable, transferable hand in hand to a social meeting, and contextualized. Thus, it is part of the physical universe, and content diversity or its remarkability is typically associated with its diversified nature and physical environment. One must first understand how the initiative is defined to grasp the complete picture of Industry 5.0 and its implications.
Understanding What Industry 5.0 Entails In The New Digital Business Revolution
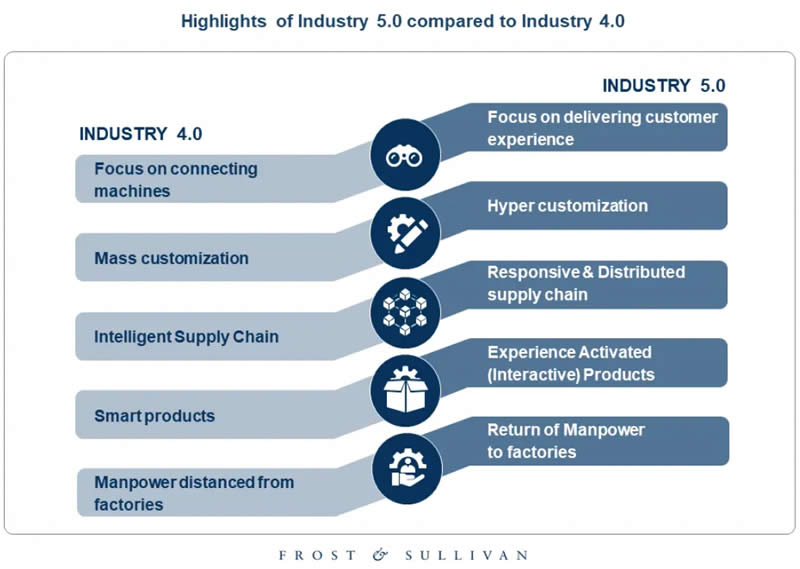
The term Industry 5.0 refers to people working alongside robots and intelligent machines. It’s about robots helping humans work better and faster by leveraging advanced technologies like the Internet of Things (IoT) and big data. It adds a personal human touch to the Industry 4.0 pillars of automation and efficiency. Most machines in the workplace have become more intelligent and connected.
As such, Industry 5.0 aims to merge those cognitive computing capabilities with human intelligence and resourcefulness in collaborative operations. In manufacturing environments, robots have historically performed dangerous, monotonous, or physically demanding work, such as welding and painting in car factories and loading and unloading heavy materials in warehouses.
Latest developments in RFID, smart sensors, communication technologies, and Internet protocols enable the role of IoT technology in driving businesses. On that note, the basic premise is to have intelligent sensors collaborate directly without human involvement to deliver a new class of applications. There’s a new revolution in Internet, mobile, and machine-to-machine (M2M) technology.
All these can be seen as the first phase of the IoT. In the coming years, the IoT is expected to bridge diverse technologies to enable new applications by connecting physical objects to support intelligent decision-making. Some MQTT servers and simple IOT applications help to analyze received sensor data and control devices. So, how do Industry 4.0 and Industry 5.0 technology merge?
How Technology-Driven Industry 4.0 Is Transitioning Into Industry 5.0
The Danish company Universal Robots claimed to be the first industrial robot provider that works safely and effectively alongside humans. Whereas industrial robots have traditionally operated separately from workers and behind safety cages, the company’s robots were first deployed alongside human workers in 2008 at Linatex, a technical plastics and rubber supplier for industrial applications.
The pairing of human and machine workers opens the door to countless opportunities in manufacturing and other related segments. And since the use cases of Industry 5.0 are still in their relative infancy, manufacturers should be actively strategizing ways to integrate human and machine workers to maximize the unique benefits that can be reaped as the movement continues to evolve.
In 2011, the vision of Industry 4.0, initially meant for the German (manufacturing) industry, was officially presented at the Hannover Messe fair. In 2017, Japan shared its vision of a concept called Society 5.0 at the CeBIT fair in Germany. And for several years, you might have come across the term Industry 5.0. If you haven’t yet, you undoubtedly will.
Perhaps it all becomes confusing, so here’s what you need to know. Industry 4.0 is essentially driven by cyber-physical convergence, enabled by IoT (the Internet of Things), supporting technologies, digit(al)ization, automation, and the convergence of IT and OT (short for operational technology but also about people and teams specialized in it, like with IT).
There are more technologies and elements, such as cyber-physical systems, horizontal and vertical integration, the move from industrial automation to digital transformation, connected value chains, and more. Although this originally wasn’t sure, the vision of Industry 4.0 is also tied to the notion of a fourth industrial revolution in which we live.
How Technology Is Helping Revolutionize The New Industry 5.0 Era
With evolving technologies, it is possible to connect the real world with the virtual world using intelligent-driven sensors or physical objects. The Internet of Things (IoT) is one such technology. The rise of interest in IoT is leading to a new era in which all objects, devices, and sensors are connected over the Internet. This will change the pattern of how we collect and analyze data.
In particular, to help make our systems more efficient. This will, in turn, improve the quality of mankind. Using IoT, the user can communicate and control physical devices. This survey paper compares major protocols like MQTT, AMQP, CoAP, XMPP, HTTP/HTTPS, RESTFUL SERVICES, and WEBSOCKETS. Comparison of IoT protocols is done based on facts.
Such as parameters like what type of transport, security, Architectural style it provides, and how it works in Low-power and lossy networks. We are intrigued whether the protocol supports Publisher/Subscriber mode or Request/Response mode for communication. We have also seen some major cloud platforms that are used in IoT, like AWS, AZURE, and Firebase cloud computing.
Resource discovery is a crucial concept enabling more innovative interactions and communications between IoT artifacts. The ultimate objective of resource discovery in IoT environments is to find devices and services of interest to the requesting entity. The unique characteristics of IoT environments pose additional challenges to resource discovery. But there are other benefits.
1. Supply Chains And Blockchain Technologies
Once used exclusively for purchasing and selling bitcoins, blockchain technologies have entered the mainstream of computer applications, fundamentally changing how Internet transactions are often implemented by ascertaining trust between unknown parties. Additionally, they ensure immutability and enable disintermediation.
These advantages can produce disruptive changes, inspiring many applications when adequately exploited. These applications form the backbone of the web of value to bring significant changes like those brought over the last 25 years by the traditional Internet. It’s indisputable that artificial intelligence and blockchain conception are escalating at an outstanding rate.
Both techniques have distinct degrees of multi-dimensional and technological complexity and business implications. So, the standard misunderstandings about the Blockchain conception, specifically, in “a Blocking chain is separated and then no one jurisdiction it.” But the fundamental evolution of a Blocking chain system continues to be ascribed to many core developers.
2. Global Internet Communication Access Networks
Current wireless sensor devices face many issues integrating with the global internet communication networks due to incompatible Application messaging protocols. Various heterogeneous application messaging protocols like HTTP, MQTT, COAP, DDS, and AMQP are available. Each application messaging protocol is designed and implemented per different application requirements.
At the same time, while considering the computational resources and available communication bandwidth. These protocols are unsuitable for constrained sensor devices due to computational power and bandwidth limitations. MQTT protocol is designed and implemented for Machine-to-machine communication, but it is still problematic for low-power sensor devices.
Partially, this is due to the complexity of the TCP transport protocol used. A more efficient MQTT-SN protocol is (Message Queue Telemetry Transport-Sensor Network) proposed for sensor devices considering the wireless sensor network characteristics, power constraints, and bandwidth limitations. MQTT-SN messages are transported using less overhead UDP Transport Protocol.
3. A True IoT Essence Implementation Analogy
Another example is the Internet of Things (IoT) in this analogy. It’s expected to become a driver in an emerging era of an interconnected world through the advanced connectivity of smart devices, systems, and services. IoT goes beyond a broad range of Machine-to-Machine (M2M) communication technologies and covers various networking protocols. Today, multiple solutions exist.
Like MQTT or SIP collecting data from sensors, CoAP for constrained devices and networks, or XMPP for interconnecting devices and people. There is also a plethora of standards and frameworks (OSGi, AllJoyn) bringing closer the paradigm of IoT vision. However, the primary constraint of most existing platforms is their limited mutual interoperability. The IoT vision is crystal clear.
It states that sensors and actuators should be integrated into the internet to facilitate interactions with the physical environment. Novel Low Power Wide Area Network (LPWAN) technologies have arisen to facilitate the interconnection of many sensors at a large scale, providing low-cost implementation and comprehensive coverage.
4. Identifying And Monitoring Botnet Commands
The botnet is one of electronic information and technology’s most substantial threats. Because all people throughout the world are discovering innovations, offenders are exploring new tools to offer crime in different meanings. It is unnecessary to be available on the web of the criminal act due to the development of tech offenders. Intruders can target potential users directly.
And then take hold of their passwords to perform multiple harmful operations. Original bots that evolved throughout the Web’s early years were malignant. The botnet, a system of web-connected manipulating computers operated by an intruder, is known as one of the most devastating risks to security. Sometimes, a machine may be damaged by a drive-by-download.
Something that has integrated malware becomes a botnet member. A bot usually runs concealed and communicates in its operational server using a secret network. Botnets are managed by protocols like Internet Relay Chat and Hyper Text Transfer Protocol (HTTP) and in a protocol-consistent way, rendering it a complicated issue to identify and monitor the botnet command.
On that note, this research paper gives a comprehensive overview of Botnet detection techniques followed by their merits, demerits, and features employed in various methods.
5. Data Security Essentials, Attacks Detection & Prevention
Human advancement is moving towards being more associated with nature. It was confirmed even 10 years before the electrical message was invented. From that point forward, there was no stop for humans to associate everything through electrical/electronic and computerized channels. That’s why, as of late, the business sector has named it IoT, characterized as the Internet of Things.
The name characterizes its temperament as its Inter associating the “things.” You can substitute any usable item interconnected as a “thing,” i.e., mechanical articles like vehicles, electrical articles like fans, TVs, etc. This opens up many occasions to taunt any “things” on the web, permitting outsiders to assume control over the control. Every second, a massive amount of data is transmitted.
It’s then securely saved from many resources. Data security, otherwise called network protection, means” measures taken to ensure a PC or PC framework (as on the Internet) against unapproved access or attack.” Markedly, password securing our workstations and work telephones are instances of information security. Individuals and organizations do this for a more extensive scope.
In particular, to help them shield touchy individual and business data from being spilled. Fortunately, this review paper will assist with examining the dangers associated with data security and review the techniques related to data security and attack detection mechanisms.
6. Smart Heart Rate Sensing And Monitoring Technology
In this case, intelligent healthcare technology is most needed to deploy an effective healthcare system because of its faster medical response. With the help of smart wearable devices, medical data can be uploaded to cloud health records, providing doctors access to monitor the patient’s health in real time. Therefore, competent healthcare is achieved.
Though at a low cost, the healthcare industry produces many smart devices. An essential challenge in heart rate monitoring is integrating several smart devices and protocols within the network, which remains tedious. For instance, smartphones used to collect data make connecting with that particular network and other communication protocols difficult.
As a result, this further complicates the process of aggregating the information. For your information, this paper aims to evaluate a heart rate monitoring information system. More so based on IoT where reliability metric to the design process is in focus.
7. Real And Accurate Cloud-Based Fraud Detection Systems
Over the last decades, deep and machine learning techniques have achieved prominent outcomes in various areas like data analytics, big data processing, and cloud classifications. This makes real-time intelligent models. A particular investigation proposes a cloud-based fraud detection system using Fully Convolution Neural Networks (FCNN).
Along with this deep learning, Gradient Boosting Machine Learning (GBML) technology is incorporated; it permits real-time fraud classification and regression on clouds. Perse, in this review article, you can look at our proposed methodology, FCNN, and GBML, which competes with existing models regarding the accuracy, recall, actual positive rate, and precision.
8. Effective Smart Environment Communication Protocols
Smart home IoT networks have been recognized as a standard and part of daily life in the coming 5G Network era. Users use Internet of Things (IoT) sensors in everyday routines to control home services through remote access anywhere, anytime. Without being protected, network management can cause smart home networks to be vulnerable to various security threats.
Protecting data traffic transmitted between user mobile devices and their in-home IoT appliances is essential because it includes users’ sensitive and critical privacy information. To overcome this problem, a new method known as a Lightweight and Robust mutual authentication scheme (LRMA) for protecting distributed innovative environments from unauthorized abuses is proposed.
In an intelligent environment, smart devices use implicit certificates and enable mutual authentication and key agreement. Computation and communication complexities are reduced for efficiency, and LRMA resists attacks. Moreover, both security analysis and performance evaluation prove the effectiveness of LRMA as compared to the state-of-the-art schemes.
9. Convolutional Neural Networks For Identifying Emotions
In modern times, machine learning is a flourishing technique employed in computer vision, digital image processing, and many other fields. Machine learning concepts are also used in neural networks while studying convolutional neural network (CNN) models to spot and analyze images and identify facial expressions.
In this review article, we’ve got surprising results, like how the detection of face expression recognition is practicable in teaching. Therefore, this method helps teachers to vary their teaching methodology by observing students’ expressions. This paper presents how students’ emotions are recognized from their faces. As such, it includes three steps:
First is face detection using Haar Cascades techniques, second is normalization and third is emotion recognition using a convolutional neural networks model. It then helps analyze seven sorts of facial expressions.
10. Using Cryptographic Hash Codes To Verify Node Credentials
Ad hoc networks are vulnerable to attacks due to the mobility of nodes in a dynamic network where nodes can position at any point in time. In MANeT, a lot of attacks can be initiated, but most of them are comparatively easy to detect because of their property of dramatically changing the network data.
When considering the security issues of MANET, it is vital to consider wormhole attacks. A wormhole attack is complex to detect & can spoil important data by directing it to illegal nodes. It consists of two malicious nodes and a tunnel among them through which an attacker tunnel the data.
In the route discovery process, a wormhole can relay route request and response messages between faraway nodes, manifesting a shorter path to the destination. Since the wormhole can be anywhere along the way, a source must identify it when a node sets up the route.
Many protocols have been proposed, and their confrontation with various types of security attacks and efficiency are critical points of concern in implementing these protocols. We can use cryptographic hash code to verify the credentials of each node and lure the faulty node with the pre-known route to remove the malicious node from the network.
The Topmost Critical IoT Initiatives And AI Integration Elements
Driverless cars with artificial intelligence (AI) and automated supermarkets run by collaborative robots (cobots) working without human supervision have sparked off new debates: What will be the impacts of extreme automation, turbocharged by the Internet of Things (IoT), AI, and the Industry 4.0, on Big Data and omics implementation science?
The IoT builds on;
- broadband wireless internet connectivity,
- miniaturized sensors embedded in animate and inanimate objects ranging from the house cat to the milk carton in your smart fridge,
- AI and cobots making sense of Big Data collected by sensors.
Industry 4.0 is a high-tech strategy for manufacturing automation that employs the IoT, thus creating the Smart Factory. Extreme automation until “everything is connected to everything else” poses vulnerabilities that have been little considered. First, highly integrated systems are vulnerable to systemic risks such as total network collapse if one of its parts fails.
For example, hacking or Internet viruses can fully invade integrated systems. Second, extreme connectivity creates new social and political power structures. If left unchecked, they might lead to authoritarian governance by one person in total network power control, directly or through her/his connected surrogates. We propose Industry 5.0 can democratize knowledge.
Especially in terms of coproduction from Big Data, building on the new concept of symmetrical innovation. Industry 5.0 utilizes IoT but differs from predecessor automation systems by having three-dimensional (3D) symmetry in innovation ecosystem design.
Consider the following:
- A built-in safe exit strategy in case of hyperconnected entrenched digital knowledge networks demise. Notably, such safe exists are orthogonal in that they allow “digital detox” by employing pathways unrelated/unaffected by automated networks, for example, electronic patient records versus material/article trails on vital medical information.
- Equal emphasis on both acceleration and deceleration of innovation if diminishing returns become apparent;
- Next generation social science and humanities (SSH) research for global governance of emerging technologies: “Post-ELSI Technology Evaluation Research” (PETER). Importantly, PETER considers the technology opportunity costs, ethics, ethics-of-ethics, framings (epistemology), independence, and reflexivity of SSH research in technology policymaking.
Industry 5.0 is poised to harness extreme automation and Big Data with safety, innovative technology policy, and responsible implementation science enabled by 3D symmetry in innovation ecosystem design. To be prepared for Industry 5.0 and its impacts, there are three critical elements of the initiative that you must understand.
#1 Industry 5.0 is aimed at supporting – not superseding – humans
Don’t mistake the upsurge in robotics as an opportunity to eliminate headcount and replace workers who perform repetitive tasks on assembly lines. Manufacturers who understand the value of human intuition and problem-solving capabilities are positioning themselves to thrive. Most people often think of manufacturing workers as a poor substitute for a robot.
But these things are complicated in practice, and the assembly line worker often makes judgments. And it turns out that when you take that person away, you end up with problems that are hard to solve. Even Tesla CEO Elon Musk admitted that “excessive automation” at his company was a mistake, tweeting that “Humans are underrated.”
While robots are much more consistent than humans and better at precision work, they’re inflexible and incapable of the adaptability and critical thinking that define us as humans. Working together with people, robots can fulfill their designated purpose of providing assistance and making our lives better. Universal Robots uses the term collaborative robots (cobots) in digital space.
This helps to emphasize the importance of people in robotic technology. Industry 5.0 will make the factory a place where creative people can come and work to create a more personalized and human experience for workers and their customers,” said Esben Østergaard, Universal Robots chief technology officer and co-founder, in an article published on Enterprise IoT Insights.
#2 Industry 5.0 is about finding optimal efficiency and productivity
The objective of Industry 4.0 is to interconnect machines, processes, and systems for maximum performance optimization. Industry 5.0 takes such efficiency and productivity a step further. It’s about refining the collaborative interactions between humans and machines.
KUKA, one of the world’s leading suppliers of intelligent automation solutions, finds that diverse business sectors — from the automotive industry to timber construction companies — benefit from the principles and products engendered by Industry 5.0. But their gains haven’t been achieved without some initial hesitations.
Employees at Müllerblaustein, a timber construction firm that has teamed with KUKA on Industry 5.0-related initiatives, at first were skeptical about using robots that could potentially take their jobs away, according to the company’s managing director, Reinhold Müller. But those fears faded once the efficiency advantages became evident.
“In production operations, they realized that the robots relieve them of physically demanding work, and they can concentrate on other tasks,” Müller said. “Craftsmanship and robotics complement each other ideally here.”
Rogers Corporation, a manufacturer of specialty materials used in consumer and electronic products, is another company that evangelizes the upsides of Industry 5.0. The manufacturer reports its capacity to dramatically improve efficiency by integrating robots into its manufacturing processes. The company’s website touts a variety of robotics applications, including one that features a robot performing a task while a camera system records visual data. Using this system, a worker can complete several tasks simultaneously via robots, and if the camera notes any visual discrepancies, the worker is notified so corrections can be made.
“Industry 5.0 recognizes that man and machine must be interconnected to meet the manufacturing complexity of the future in dealing with increasing customization through an optimized robotized manufacturing process,” said Marc Beulque, vice president of global operations at Rogers.
#3 The progress of Industry 5.0 is unavoidable
Once you’ve used technology to make a process more efficient, there’s no point reverting to the old way of doing things. It’s why we use computers with word-processing software instead of typewriters. Similarly, Industry 5.0 is the manufacturing world’s event horizon. Given the efficiencies that can be gained, we’re well past the point of returning.
The European Economic Social Committee (EESC) summed it best: “The proliferation of robotic automation is inevitable.”
Recognizing that Europe trails the United States and China in advancing technologies such as artificial intelligence (AI), the European Union (EU) consultative body has called for accelerating regional AI and robotics development. “The EU should embrace digitalization wholeheartedly for the sake of consumers, manufacturers, and employees alike,” it said.
While Industry 5.0’s headway can’t be stalled, there are still essential questions and ramifications that must addressed by manufacturers and policymakers. Excessive automation, for instance, is an issue about which the authors of a research paper recently published in OMICS have expressed concerns — and their apprehensions appear to mirror the attitude shifts of innovators like Musk, whose once aggressive approaches to automation have since toned down.
“Highly integrated systems are vulnerable to systemic risks such as total network collapse,” according to the paper. “Extreme connectivity creates new social and political structures. If left unchecked, they might lead to authoritarian governance.”
Engaging with these and the many other challenges and opportunities Industry 5.0 invariably brings will require planning and preparation commensurate with each manufacturer’s needs and expected outcomes. It’s not a question of whether a manufacturer can benefit from its personnel working alongside robots but how they can best leverage new technologies to drive optimal outcomes from human/machine interactions.
In Conclusion;
In recent years, the Internet of Things (IoT) has become a hot research topic for extending Internet connectivity to physical devices in our day-to-day activities. IoT objects’ high diversity, properties, and capabilities pose significant challenges to realizing open and interoperable IoT platforms. The Internet of Things integrates billions of heterogeneous IoT things with the Internet.
In particular, embedded systems such as sensors and actuators are linked to improve quality of life. As such, they become the future of technologies in any field of human daily life. These IoT devices cooperate and generate valuable information to provide better services and applications to governments and society. Also, storing these data in the Cloud for monitoring is necessary.
Check the survey paper on IoT applications, new challenges, issues that arise in different fields, and IoT architectures. In addition, it focuses on the explanation of IoT protocols and their operations and functionalities. It also presents different microcontroller types used by researchers. Likewise, AWS IoT uses TLS 1.2-based authentication using Certificates and Security Keys.
For instance, you can create certificates from the AWS IoT Console or upload your certificate credentials to connect your devices with an AWS IoT Platform. Be that as it may, in the future, we expect to see more implementations of sensor data integration with more practical-oriented analytics and notification services. So, what’s your take on this? Please let us know in our comments.