Cryptography and its applications to Cybersecurity are vital as the world becomes increasingly digital, and the need for security has become ever more imperative. Essentially, the word Cryptography refers to the study of secure communications techniques. Still, Cryptography is closely associated with encryption, or the act of scrambling ordinary text into what’s known as ciphertext.
Then, it returns to ordinary text (called plaintext) when it arrives at its destination. Several historical figures have been credited with creating and using cryptography through the centuries, from Greek historian Polybios and French diplomat Blaise de Vigenère to Roman Emperor Julius Caesar—who is credited with using one of the first modern ciphers—together with Arthur Scherbius.
It’s worth noting that Scherbius created the Enigma code-breaking machine during World War Two. Likely, none of them would recognize the ciphers of the 21st century. Regarding Quantum Computing and the Threat to Card Payment using Cryptography, the ECSG previously published this follow-up article. It considers the developments made by the card payment cryptographic community.
For example, cryptography creates various encryption protocols regularly used to protect data. These include 128-bit or 256-bit encryption, Secure Sockets Layer (SSL), and Transport Layer Security (TLS). These encryption protocols protect all digital information and data, from passwords and emails to ecommerce and banking transactions. So, what is the role of Cryptography in security?
Understanding What Cryptography Means In Secure Communications Technology
Cryptography is the technique of obfuscating or coding data. It ensures that only the person who is meant to see the information–and has the key to break the code–can read it. The word is a hybrid of two Greek words: “kryptós,” which means hidden, and “graphein,” which means to write. Thus, it translates to hidden writing, but in reality, the practice involves the secure transmission of information.
Cryptography can be traced to the ancient Egyptians and their creative use of hieroglyphics. However, the art of coding has seen great strides over the millennia, and modern cryptography combines advanced computer technology, engineering, and maths—among other disciplines—to create highly sophisticated and secure algorithms and ciphers to protect sensitive data in the digital era.
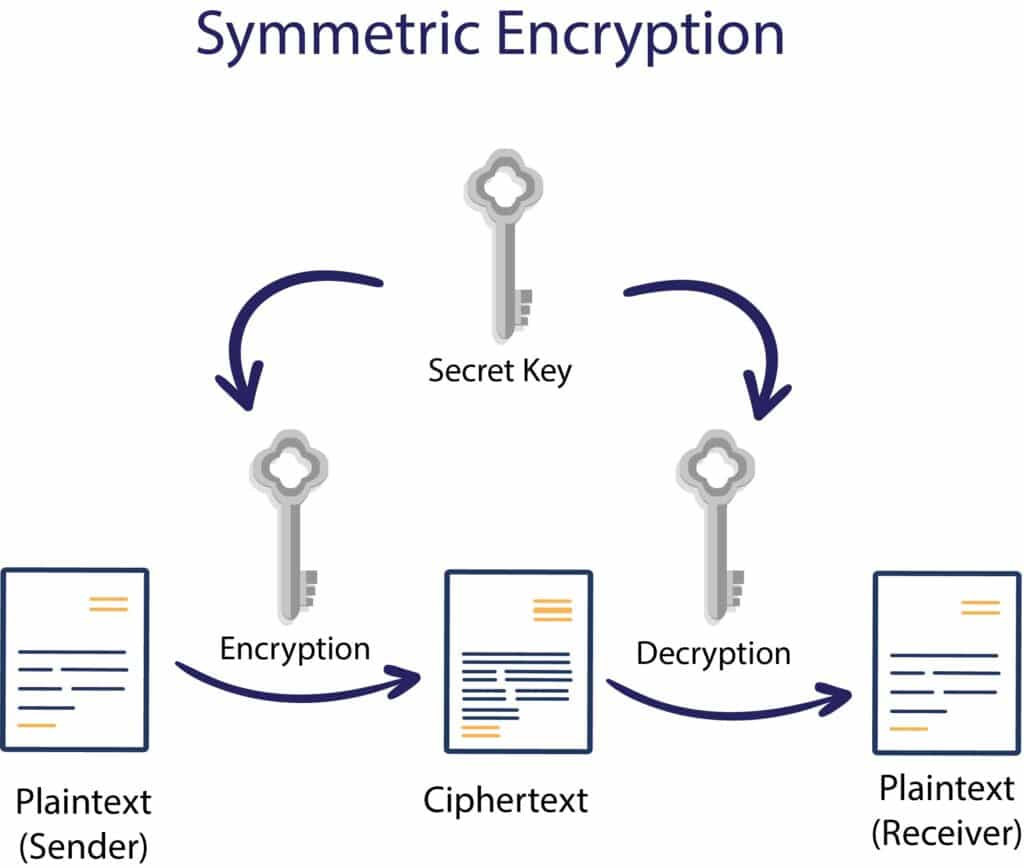
Different Cryptographic types are helpful for different purposes. For example, the simplest is symmetric key cryptography. Here, data is encrypted using a secret key, and then the encoded message and the secret key are sent to the recipient for decryption. Of course, the problem is that if the message is intercepted, the third party can easily decode the message and steal the private information.
1. Symmetric Key Cryptography
This more straightforward form of cryptography takes its name from the fact that both the sender and receiver share one key to encrypt and decrypt information. Examples are the Data Encryption Standard (DES) and Advanced Encryption Standard (AES). The sender and receiver share a single key, which the sender uses to encrypt plaintext. Still, the cipher text is sent to the receiver.
Receivers can apply this same key to decrypt the message and recover the plain text from the sender. However, the main difficulty is finding a way to share the key securely between the sender and receiver. Symmetric encryption is sometimes called secret key cryptography because one single—purportedly—secret key is used to encrypt and decrypt information. There are several forms.
They Include:
- Stream Ciphers: These work simultaneously on a single data byte and regularly change the encryption key. In this process, the keystream can be in tandem with—or independent of the message stream. This is called self-synchronizing or synchronous.
- Block Ciphers: This type of cryptography—which includes the Feistel cipher—codes and decodes one block of data at a time.
2. Public Key Cryptography (PKI)
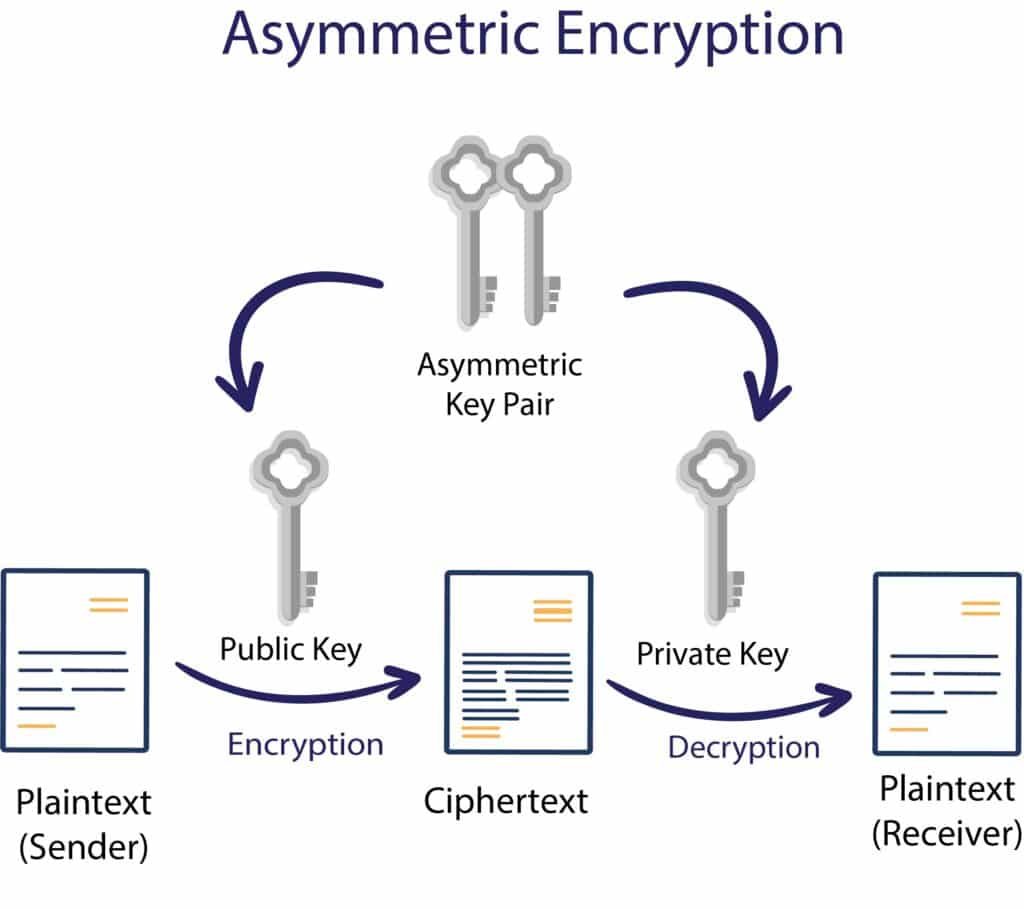
Also known as Asymmetric Cryptography, there are two related keys—public and private—which are more secure types of cryptography. It involves both the sender and receiver having two public and private keys. During the process, the sender will use the receiver’s public key to encrypt the message, while the receiver will use their private key to decrypt it.
The two keys are different, and since only the receiver will have the private key, they will be the only ones able to read the information. The RSA algorithm is the most popular form of asymmetric cryptography. While the public key may be freely distributed, the paired private key must remain confidential. The public key is used for encryption, and the private key is used for decryption.
3. Hash Function Cryptography
These are types of cryptographic algorithms that do not involve using keys. Instead, a hash value—several fixed lengths that act as a unique data identifier—is created based on the length of the plain text information and used to encrypt the data.
This is commonly used by various operating systems to protect passwords, for example. No key is used in this algorithm, but a fixed-length value is calculated from the plaintext, making it impossible to recover its contents. Computer systems often use hash functions to encrypt passwords. A popular hash algorithm is 256-SHA.
4. Asymmetric Key Cryptography
Generally, Asymmetric cryptography—sometimes called public-key encryption—hinges on the receiver having two keys in play: public and private. The sender uses the first to encode the information, while the receiver uses the latter—which only they have—to decrypt the message securely. Markedly, Asymmetric key cryptography encrypts and decrypts messages using algorithms.
Asymmetric key cryptography is based on various mathematical principles, such as multiplication or factorization—multiplying two big prime numbers to generate one massive, random number that is incredibly tricky to crack—or exponentiation and logarithms, which create exceptionally complex numbers that are nearly impossible to decrypt, such as in 256-bit encryption.
The Types:
- Rivest-Shamir-Adleman (RSA): The first type of asymmetric cryptography to be created, RSA is the basis of digital signatures and key exchanges, among other things. The algorithm is based on the principle of factorization.
- Elliptic Curve Cryptography (ECC): Often found in smartphones and on cryptocurrency exchanges, ECC employs the algebraic structure of elliptic curves to build complex algorithms. Significantly, it does not require much storage memory or usage bandwidth, making it especially useful for electronic devices with limited computing power.
- Digital Signature Algorithm (DSA): Built on the principles of modular exponentiations, DSA is the gold standard for verifying electronic signatures and was created by the National Institute of Standards and Technologies.
- Identity-based Encryption (IBE): This unique algorithm negates the need for a message recipient to provide their public key to the sender. Instead, the sender uses a known unique identifier—such as an email address—to generate a public key to encode the message. A trusted third-party server generates a corresponding private key for the receiver to decrypt the information.
Technically, to create a more secure encoding system, cryptologists devised asymmetric cryptography, sometimes known as the “public key” system. In this instance, all users have two public and private keys. When creating a coded message, the sender will request the recipient’s public key to encode the message. This way, only the intended message recipient’s private key will decode it.
As a result, even if the message is intercepted, a third party cannot decode it. A cryptosystem is used to manage cryptographic keys, including generation, exchange, storage, use, revocation, and replacement of the keys.
How Public-Private Key Encryption Works
- The Bitcoin network issues all users a private key (essentially a solid password) from which it cryptographically generates a linked public key. You can freely give people your public key. That’s the only information anyone needs to send you Bitcoin. But to access those funds, the private key is required.
- Part of what makes Bitcoin revolutionary is its solution for the double-spend problem: A peer-to-peer network that uses cryptographic methods to verify the authenticity of transactions.
- Your public key is generated from your private key via a method called “hashing,” which takes a string of data and processes it through an algorithm. It’s virtually impossible to reverse this process so nobody can guess your private and public keys.
- Because your public and private keys are linked, the network knows that your Bitcoin belongs to you – and will remain yours as long as you have your private key.
- Another impact of not having an intermediary is that Bitcoin transactions are irreversible (no credit card company to call if you make a mistake). But this is a feature, not a bug: permanent transactions are vital to solving the double spending problem.
- The other half of the solution is the Bitcoin blockchain, which is a giant, decentralized ledger – imagine a bank’s balance books – that documents every transaction and is constantly verified and updated by all the computers in the network.
Why Cryptography Is Essential In Empowering The Cybersecurity Technology
Cryptography definitions are, understandably, quite broad. This is because the term covers a wide range of different processes. As mentioned, there are many different types of cryptographic algorithms, each offering varying levels of security depending on the type of information being transmitted. TLS/SSL Certificates frequently use RSA Keys, and there are recommended key sizes.
Their use continually increases (e.g., 1024 bits to 2048 bits). This helps to maintain sufficient cryptographic strength. An alternative to RSA is ECC, which can offer the same level of Cryptographic strength at much smaller key sizes, offering improved security with reduced computational and storage requirements. Interest in using cryptography grew with the development of computers.
As well as their connections over an open network. Over time, it became apparent that there was a need to protect information from being intercepted or manipulated while being transmitted over this network. IBM was an early pioneer in this field, releasing its “Lucifer” encryption in the 1960s—this eventually became the first Data Encryption Standard (DES).
Regarding the ever-evolving digital world, cryptography is an essential cybersecurity tool. Its use means that data and users have an additional layer of security that ensures privacy and confidentiality and helps keep data from being stolen by cybercriminals. At the same time, hash functions ensure data integrity is maintained in cryptography’s encryption and decryption phases.
Other Benefits:
- Confidentiality: Only the intended recipient can access and read the information, so conversations and data remain private.
- Data Integrity: Cryptography ensures that the encoded data cannot be modified or tampered with en route from the sender to the receiver without leaving traceable marks— an example is digital signatures.
- Authentication: Identities and destinations (or origins) are verified.
- Non-Repudiation: Senders become accountable for their messages since they cannot later deny that the message was transmitted—digital signatures and email tracking are examples.
As our lives become increasingly digital, the need for cryptography to secure massive amounts of sensitive information has become even more imperative. Now, there are many ways in which cryptography is crucial in the online space. Encryption is essential to being online since so much sensitive data is transmitted daily. There are a few notable real-life cryptography applications.
Including:
- Using Virtual Private Networks (VPNs) or protocols such as SSL to browse the internet safely and securely. Or creating limited access controls so that only individuals with the correct permissions can carry out specific actions or functions or access particular things.
- End-to-end encryption includes various online communication types, including emails, login credentials, and even text messages—such as WhatsApp or Signal. Cryptography protects users from various cyberattacks, such as man-in-the-middle attacks.
- It also allows companies to meet legal requirements, like the General Data Protection Regulation (GDPR) data protection. These tools are also helpful in creating and verifying credentials, especially with strong passwords or login details.
- They also allow the secure management and transaction of Cryptocurrencies. In addition, they also enable digital signatures to sign online documents and contracts securely. As well as verify identities when logging into online accounts.
On the one hand, software systems often have multiple endpoints, typically multiple clients and one or more back-end servers. These client/server communications occur over networks that cannot be trusted. On the other hand, communication occurs over open, public networks such as the Internet or private networks, which external attackers or malicious insiders may compromise.
The Topmost Common Cryptographic Attacks You Should Know About
The cryptography tools mentioned above can help protect communications that traverse untrusted networks. An adversary may attempt to carry out two main types of attacks on a network. Passive attacks involve an attacker simply listening to a network segment and attempting to read sensitive information as it travels. Passive attacks may be online (attackers read traffic in real-time).
Or, rather, they may also be offline (an attacker captures traffic in real-time and views it later—perhaps after spending some time decrypting it). Active attacks involve an attacker impersonating a client or server, intercepting communications in transit, and viewing and modifying the contents before passing them on to their intended destination (or dropping them entirely).
In most cases, the confidentiality and integrity protections offered by cryptographic protocols such as SSL/TLS can protect communications from malicious eavesdropping and tampering. Authenticity protections ensure that users are communicating with the systems as intended. For example, are you sending your online banking password to your bank or someone else?
It can also be used to protect data at rest. Data on a removable disk or database can be encrypted to prevent disclosing sensitive data should the physical media be lost or stolen. In addition, it can also provide integrity protection of data at rest to detect malicious tampering. Usually, there are a few potential issues for cloud computing technology webmasters to watch out for.
Cryptographic attack routes:
- Weak keys: Keys are a collection of random numbers used with an encryption algorithm to alter and disguise data to make it incomprehensible to others. Longer keys involve more numbers, making them much trickier to crack—therefore, better for protecting data.
- Misusing keys: Keys must be used correctly; if not, hackers can easily crack them to access the data they are supposed to protect.
- Reusing keys for different purposes: Like passwords, each key should be unique—using the same key across different systems weakens the ability of cryptography to protect data.
- Not changing keys: Cryptographic keys can quickly become outdated, so updating them regularly to keep data secure is essential.
- Not storing keys carefully: Ensure that keys are kept in a secure place where they cannot be found; otherwise, they can be stolen to compromise the data they protect.
- Insider attacks: Keys can be compromised by individuals who legitimately have access to them—such as an employee— and sell them on for nefarious purposes.
- Forgetting the backup: Keys should have a backup because if they suddenly become faulty, the data they protect could become inaccessible.
- Recording keys incorrectly: Manually entering keys into a spreadsheet or writing them down on paper may appear logical, but it is also prone to error and theft.
Specific cryptography attacks are also designed to break through encryptions by finding the right key. An external party can crack the coding and read the protected data if the keys are compromised.
Cryptographic attack types:
- Ciphertext-only attacks: These are attacks that involve a third party intercepting the encrypted message—not the plaintext—and trying to work out the key to decrypt the information and, later, the plaintext.
- Chosen ciphertext attack: The opposite of a chosen plaintext attack, the attacker analyses a ciphertext section against its corresponding plaintext to discover the key.
- Brute force attacks: Brute force attacks are broad attacks that randomly try to guess private keys using the known algorithm.
- Chosen plaintext attack: The third party chooses the plaintext for a corresponding ciphertext to work out the encryption key.
- Known plaintext attack: In this case, the attacker randomly accesses part of the plaintext and part of the ciphertext and begins to figure out the encryption key. This is less useful for modern cryptography as it works best with simple ciphers.
- Algorithm attack: In these attacks, the cybercriminal analyzes the algorithm to try to work out the encryption key.
So, is it possible to mitigate the threat of cryptography attacks? There are a few ways in which individuals and organizations can try to lower the possibility of a cryptographic attack. Essentially, this involves ensuring the proper management of keys so that they are less likely to be intercepted by a third party or useable even if they do.
Tips To Mitigate Cryptography Attacks:
- Use one key for each specific purpose, such as unique keys for authentication and digital signatures.
- Protect cryptographic keys with more vital Key-Encryption Keys (KEKs).
- Use hardware security modules to manage and protect keys—like regular password managers.
- Ensure that keys and algorithms are regularly updated and encrypt all sensitive data.
- Create solid and unique keys for each encryption purpose.
- Store keys securely so third parties cannot easily access them.
- Ensure the correct implementation of the cryptographic system.
- Include cryptography in security awareness training for employees.
A secure system should provide several assurances, such as confidentiality, integrity, and availability of data, as well as authenticity and non-repudiation. When used correctly, cryptography helps to provide these assurances. It can ensure the confidentiality and integrity of data in transit and at rest. Or authenticate senders and recipients to one another and protect against repudiation.
In Conclusion;
Most people will not need to have more than a basic understanding of what cryptography is. However, learning the definition of cryptography, how the process works, and its cybersecurity applications can help us be more mindful about managing day-to-day digital interactions. This can help most people keep their emails, passwords, online purchases, and banking transactions.
Notwithstanding, these are all standard processes that use cryptography in their security features—making them more secure. From the above, it is clear that the main difference between symmetric and asymmetric encryption in cryptography is that the first only involves one key while the second requires two. As with most technologies, cryptography has become increasingly sophisticated.
But that does not mean that these encryptions cannot be broken. In layman’s language, the most essential principle to remember is that you should never attempt to design your cryptosystem. For a cryptosystem to be deemed “secure,” it must face intense scrutiny from the security community. Never rely on security through obscurity or the fact that attackers may not know your system.
Malicious insiders and determined attackers will attempt to attack your system. On that note, the keys should only be “secret” in a secure cryptosystem. Be sure to take appropriate steps to protect your systems’ keys. Never store encryption keys in clear text and the data they protect. This is akin to locking your front door and placing the key under the doormat—the first place attackers look.