According to the TechTarget team, Two-Factor Authentication (2FA) has long been used to control access to sensitive systems and data. For this reason, a majority of online service providers are increasingly using 2FA to protect their users’ credentials from being used by hackers who stole a password database. They also use phishing campaigns to obtain user passwords.
However, as far as SFA services go, usernames and passwords are not the most secure. Since there is just one problem with password-based logins. And, that’s to say that their authentication often requires knowledge and diligence to create and remember strong passwords. Passwords often require user protection from many external or even insider security threats.
Such as carelessly storing sticky notes with login credentials, old hard drives, and social engineering exploits. Preying on passwords is very common when it comes to external security breaches. For instance, such as where cybercriminals/hackers use brute force, dictionaries, or rainbow tables to initiate system infiltration attacks. And they, eventually, steal critical data.
Given enough time and resources, an attack hacker can usually breach password-based security systems and steal corporate data. Passwords have remained the most common form of SFA. Obviously, because of their low cost, ease of implementation, and familiarity. And as such, that’s where the Two-Factor Authentication (2FA) factors come in handy as you’ll learn.
What A Two-Factor Authentication (2FA) Is All About
By definition, Two-Factor Authentication (2FA), sometimes referred to as Two-Step Verification or Dual-Factor Authentication, is a security process in which users provide two different authentication factor methods to verify themselves. Technically, the verification implementation process is for better protecting both users’ data and access to resources.
Two-factor authentication provides a higher level of security than authentication methods that depend on Single-Factor Authentication (SFA), in which the user provides only one factor — typically, a password or passcode. The authentication methods rely on a user providing a password as the first factor. And also a different security token as a second factor.
Or rather, some biometrics factor, such as a fingerprint or facial scan. Two-factor authentication adds an additional layer of security to the authentication process by making it harder for attackers to gain access to a person’s devices or online accounts because, even if the victim’s password is hacked, a password alone is not enough to pass the authentication check.
In other words, a 2FA is a form of MFA. To enumerate, a Multifactor Authentication (MFA) is a security technology that requires multiple methods of authentication. In particular, from independent categories of credentials — to verify a user’s identity.
Either for login or other transactions. Technically, it is in use any time two authentication factors are required to gain access to a system or service. However, using two factors from the same category doesn’t constitute 2FA. For example, requiring a password and a shared secret is still considered SFA. Since they both belong to the knowledge authentication factor type.
How The Most Common Multistep Process Works
Firstly, the platform user is prompted to log in by the application or the website. Secondly, the user enters what they know — usually, a username and password combination. And then, the site’s server finds a match and recognizes the user. Sometimes, there are processes that don’t require passwords, where the website generates a unique security key for the user.
As a result, the authentication tool processes the key, and the site’s server validates it. The site then prompts the user to initiate the second login step. Although this step can take a number of forms, the user has to prove that they have something only they would have, such as biometrics, a security token, an ID card, a smartphone, or other mobile devices.
For your information, this is what some gurus will call an inherence or possession factor. Then, thereafter, the user may have to enter a one-time code that was generated during step four. And, after providing both factors, the user is authenticated and granted access to the application or website. Perse, there are many different devices and services for implementing 2FA.
From Radio Frequency Identification (RFID) to token cards to smartphone apps. The authentication code is a short sequence linked to a particular device, user, or account. And, it can be used only once as part of any given authentication process. On that note, two-factor authentication products can further be divided into two major categories as per their work.
Consider the following:
- tokens that are given to users to use when logging in; and
- infrastructure or software that recognizes and authenticates access for users who are using their tokens correctly.
Multiple challenge-response questions can provide more security, depending on how they are implemented, and standalone biometric verification methods can also provide a more secure method of SFA. Enabling two-factor authentication varies depending on the specific application or vendor. However, the processes can involve the same general, multistep process.
Authentication tokens may be physical devices, such as key fobs or smart cards, or they may exist in software such as mobile or desktop apps that generate PIN codes for authentication. These authentication codes, also known as One-Time Passwords (OTPs), are usually generated by a server and can be recognized as authentic by an authentication device or app.
The Basic Authentication Factors You Should Know
Organizations need to deploy a system to accept, process, and allow or deny access to users authenticating with their tokens. This may be deployed in the form of server software or a dedicated hardware server, as well as provided as a service by a third-party vendor. An important aspect of 2FA is ensuring that the authenticated user is given access to all resources.
Resources that the user is approved for and only those resources. As a result, one key function of 2FA is linking the authentication system with an organization’s authentication data. Microsoft provides some of the infrastructure necessary for organizations to support 2FA in Windows 10 through Windows Hello, which can operate with Microsoft accounts.
As well as authenticate users through Microsoft Active Directory, Azure AD, or Fast IDentity Online (FIDO). There are several ways that we can be authenticated by using more than one authentication method. Currently, most authentication methods rely on knowledge factors. Such as a traditional password, while 2FA methods add either a possession or inherence factor.
Similarly, Three-Factor Authentication (3FA) is the use of identity-confirming credentials from three separate categories of authentication factors. Typically, including the knowledge, possession, and inherence categories. As of today, below are some of the most common Two-Factor Authentication (2FA) factors, listed in approximate order of adoption for computing.
Knowledge & Possession Factor
On one side, a Knowledge Factor is something the user knows. Such as a password, a personal identification number (PIN), or some other type of shared secret. While, on the other side, the Possession Factor is something the user has. Such as an ID card, a security token, a cellphone, a mobile device, or a smartphone app, to approve requests.
Biometric (Inherence) Factor
A Biometric Factor, also known as an Inherence Factor, is something inherent in the user’s physical self. These may be personal attributes mapped from physical characteristics, such as fingerprints authenticated through a fingerprint reader. Other commonly used inherence factors include facial recognition and voice recognition or behavioral biometrics as well. Some behavioral biometrics such as keystroke dynamics, gait features, and speech patterns, among others.
Location Factor & Time Factor
Usually, the Location Factor is denoted by the location from which an authentication attempt is being made. This can be enforced by limiting authentication attempts to specific devices in a particular location. Or by tracking the location of an authentication attempt based on the source Internet Protocol address or some other geolocation info.
Such as Global Positioning System (GPS) data, derived from the user’s mobile phone or other devices. As for the Time Factor, it restricts user authentication to a specific time window in which logging on is permitted. And, as a result, it restricts access to the system outside of that window.
The vast majority of two-factor authentication methods heavily rely on the first three authentication factors — Knowledge, Possession, and Biometric (Inherence) Factor. Moreover, systems requiring greater security may use them to implement Multifactor Authentication (MFA), which can rely on two or more independent credentials — for more secure authentication.
What Role Do The 2FA Hardware Tokens Play?
2FA hardware tokens are available supporting different approaches to authentication. One popular hardware token is the YubiKey, a small Universal Serial Bus (USB) that supports OTPs, public key encryption, and authentication. Plus the Universal 2nd Factor (U2F) protocol by the FIDO Alliance. YubiKey tokens are sold by Yubico Inc., based in Palo Alto, Calif.
When users with a YubiKey log in to an online service that supports OTPs — such as Gmail, GitHub, or WordPress — they insert their YubiKey into the USB port of their device, enter their password, click in the YubiKey field and touch the YubiKey button. In return, YubiKey generates an OTP and enters it in the most preferable/appropriate field.
Learn More: Using 2FA Hardware Tokens For A Two-Factor Authentication
The OTP is a 44-character, single-use password; the first 12 characters are a unique ID that represents the security key registered with the account. The remaining 32 characters contain information that is encrypted. While using a key known only to the device and Yubico’s servers — the encrypted key established during the initial account creation.
Then, the OTP is sent from the online service to Yubico for authentication checking. Once it’s validated, the Yubico authentication server sends back a message confirming this is the right token for this user — a complete 2FA. The user provides two factors of authentication: The password is the knowledge factor, and the YubiKey is the possession factor.
How The Two-Factor Authentication (2FA) Process Really Works
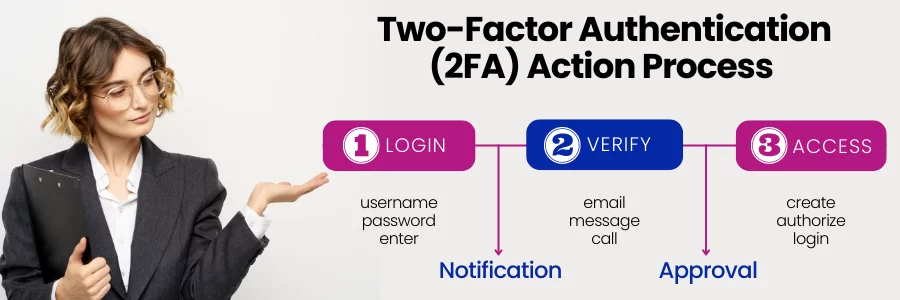
Two-Factor Authentication (2FA) works by adding an additional layer of security to online accounts. It requires an additional login credential — beyond just the username and password — to gain account access. Getting that second credential requires access to something that belongs to you. Without this additional access method, it’s impossible to access accounts.
Something — which in turn makes it impossible for hackers to access your account. More so, using only a stolen password and some key login information. With that in mind, below is a Web Tech Experts Taskforce team simplistic 2FA action diagram:
As per the Merchant Fraud Journal website blog team, the Two-Factor Authentication (2FA) process describes an approach, not a method. Not to mention, many different methods exist to secure your account with two-factor authentication.
There are three main types include:
- Additional login credentials only the account holder should know.
- The main credentials include things like security question answers and PIN numbers.
- Devices the account holder owns that receive additional login credentials.
- The user device most commonly takes the form of a security token, mobile phone app, or tablet device app.
- Biometric login credentials are unique to the account owner, such as retina scans and fingerprints.
Forthwith, you can determine which Two-Factor Authentication (2FA) method works best for you. Companies often prefer the device method, because employees may feel biometric options violate their privacy. Individuals often find it less cumbersome to secure devices they own with biometric methods, because they don’t require you to carry around multiple devices.
Two-Factor Authentication (2FA) Methods For Mobile Devices
Nowadays, most smartphone devices offer a variety of 2FA capabilities, enabling companies to use what works best for them. Some devices can recognize fingerprints, use the built-in camera for facial recognition or iris scanning, and use a microphone for voice recognition. Smartphones equipped with GPS can verify location as an additional factor.
Voice Messages or Short Message Services (SMSs) may also be used as a channel for out-of-band authentication. A trusted phone number can be used to receive verification codes by text message or automated phone call. A user has to verify at least one trusted phone number to enroll in mobile 2FA. Apple iOS, Google Android, and Windows 10 all have apps that support 2FA.
Whilst, enabling the phone itself to serve as the physical device to satisfy the possession factor. Duo Security, based in Ann Arbor, Mich. — bought by Cisco in 2018 for $2.35 billion, has a platform that enables customers to use their trusted devices for 2FA. The platform first establishes that a user is trusted before verifying that the mobile device is also safe.
Resource Guide: The Best Authenticator Apps For Android, iOS, Windows, And macOS
Chiefly, some authenticator apps may also provide a way to replace the need to obtain a verification code via text, voice call, or email altogether. For example, to access a website or web-based service that supports Google Authenticator, users type in their username and password — a knowledge factor. Users are then prompted to enter a six-digit number.
Instead of having to wait a few seconds to receive a text message, an authenticator generates the number for them. These numbers change every 30 seconds and are different for every login. By entering the correct number, users complete the verification process and prove possession of the correct device — an ownership factor.
These and other Two-Factor Authentication (2FA) products offer information on the minimum system requirements necessary to implement 2FA. With that in mind, let’s have a look at a few other most common methods of 2FA authentication so far.
1. Mobile Phone Text Messages
Text messages for two-factor authentication send a login code to a mobile device number you register with the account. This is the most streamlined form of 2FA. All you need is a cellphone and a connection to a wireless network. Text message 2FA is very common for personal accounts, but it is not without risk. Oftentimes, there’s a chance of impersonating you.
Especially, in your service carrier company. So that they can hijack your phone, and gain unauthorized access to your accounts. For this reason, such corporations should be wary of this method. Not unless employees have dedicated corporate phone lines. Routing access through an employee’s personal number risks a fired employee doing major damage.
Resource Guide: How To Track Phone Location Or Someone | Legal Ways & Best Apps
In addition, employees’ personal phone plans may not offer service everywhere, which risks an employee locking themselves out of their accounts while on an international business trip. Any good internet connection speed is enough to access your account. In addition, authentication apps like Google offer a list of backup codes to use in case of connectivity problems.
By the same token, Facebook — a recently added subsidiary of Meta — said it will make Two-Factor Authentication (2FA) mandatory for high-risk accounts likely to be targeted by malicious hackers. If you set up two-factor authentication, you’ll be asked to enter a special login code. Or confirm your login attempt each time you/someone tries accessing Facebook.
Either from a web browser or mobile device that Facebook doesn’t recognize. You can also get alerts when someone tries logging in from a browser or mobile device that Facebook doesn’t recognize.
2. Applications Plus Biometrics
On one hand, the authentication app 2FA works by using a mobile app to generate an authentication code. You must then enter this code to gain access to your account. Unlike text messages, apps don’t require the user to have access to a wireless network. On the other hand, biometric 2FA authentication works by requiring you to present something unique
Particularly, in regard to your physical person in order to gain access to your account. Common methods of biometric verification include retinal scans via a computer’s camera, or a requirement to use a fingerprint on tablets. While increasingly popular, it’s important to note limitations to these methods exist. The most common is the fear of biometric data theft.
Unlike a changeable password, stealing information about your retina or fingerprint would comprise your security and privacy for life. That’s why you should always stay vigilant in terms of the information that you share openly. On that note, we are going to let you know how you can secure yourself using the Two-Factor Authentication (2FA) process later on.
3. Passwordless Push Notifications
To enumerate, a push notification is basically a passwordless authentication that verifies a user by sending a notification directly to a secure app on the user’s device, alerting the user that an authentication attempt is happening. The user can view details of the authentication attempt and either approve or deny access — typically, with a single tap.
If the user approves the authentication request, the server receives that request and logs the user into the web app. Push notifications authenticate the user by confirming that the device registered with the authentication system — usually a mobile device — is in the possession of the user. If an attacker compromises the device, the push notifications are also compromised.
Related Topic: Push Notification | Steps To Create High Converting CTAs
The best thing about push notifications is that they help eliminate security breach risks and threats such as man-in-the-middle attacks, unauthorized access, and social engineering attacks. While push notifications are more secure than other forms of authentication methods, there are still security risks. And, they are bound to keep rising given computing advancements.
For example, users could accidentally approve a fraudulent authentication request. In particular, just because they are used to tapping on the ‘Approve’ button or a pop-up notice whenever they receive such passwordless push notifications.
Is The Two-Factor Authentication Method Really Secure?
One thing is for sure, while the 2FA process does improve security, its schemes are only as secure as their weakest component. For example, hardware tokens depend on the issuer or manufacturer’s security. The account recovery process itself can be subverted — when it’s used to defeat a 2FA action. Because it often resets a user’s current password.
And then, it emails a temporary password to allow the user to log in again, bypassing the 2FA process. One particular sample hack case is that of the business Gmail accounts of the chief executive of Cloudflare — the hack came in this way. Still, one of the most high-profile cases of a compromised two-factor system occurred in 2011. In regards to RSA Security company.
Resource Guide: Who Are Cybercriminals? How They Hack, Infiltrate & Breach Data
Whereby, RSA reported that its SecurID authentication tokens had been hacked. So, in terms of business security attack risks and data breaches, the 2FA process is still vulnerable to numerous attacks. Even though, most SMS-based businesses still see 2FA as inexpensive, easy to implement, and considerably user-friendly. In this case, please let us know what you think.
In its Special Publication 800-63-3: Digital Identity Guidelines, the National Institute of Standards and Technology (NIST) discourages the use of SMS in 2FA services. It concludes that OTPs sent via SMS are too vulnerable. Partially, due to mobile number portability and phone network attacks, or malware that can easily intercept or redirect text messages.
The Topmost Two-Factor Authentication Best User Practices
To begin with, you should never use just a username and password to protect your account. Keep in mind, that the number of corporate security breaches is on a rise. And, in recent memory, they all too well prove it is so easy for hackers to gain access to your accounts. However, that doesn’t mean that two-factor authentication is a foolproof way to prevent commerce fraud.
Always remember, that using text messages, authenticator apps, or biometric methods is better than nothing. But, you should also go beyond that and follow a few Two-Factor Authentication (2FA) best user-based practices to utilize.
Consider the following best practices:
- Don’t use your personal phone number for text 2FA authentication.
Phone carriers are notorious for getting tricked into changing account details by clever hackers. Instead, set up a dedicated Google Voice number that you can always keep and that a phone carrier cannot change. - Don’t use email-based account resets.
It’s convenient to reset your accounts by email. This is because it makes it very easy for a hacker to bypass other 2FA procedures you’ve put in place and get at the account with just a username and password. - Use a combination of authentication methods.
You can secure many accounts with more than one 2FA method. And the more 2FA methods you use, the more secure your information is.
Two-factor authentication is an essential step in knowing how to prevent eCommerce fraud. Although adding additional layers is inconvenient, it’s much less inconvenient — and costly — than a fraudster impersonating you. Or otherwise, getting access to your personal information, or stealing your bank account details in the long run.
How Is The Authentication Technology Future Like?
Environments that require a higher security may be interested in three-factor authentication, which typically involves the possession of a physical token and a password used in conjunction with biometric data, such as fingerprint scans or voiceprints. Factors such as geolocation, type of device, and time of day are also commonly used, and the demand is rising.
Overall, they help determine whether a user should be authenticated or blocked. Additionally, behavioral biometric identifiers, such as a user’s keystroke length, typing speed, and mouse movements, can also be discreetly monitored in real time. More so, in order to provide continuous authentication. Instead of a single one-off authentication login check.
This means, that we need to stop relying on passwords as the main method of authentication. In reality, passwords often no longer offer the security or User Experience (UX) that companies and their users demand. Of course, other various legacy security tools, such as a password manager and MFA, attempt to deal with the problems of usernames and passwords.
Resource Guide: Malicious Mobile Apps & Look-Alike Domain Scams Safety Guide
Unfortunately, they highly depend on essentially outdated architecture such as the password database. Consequently, many organizations are turning to passwordless authentication. Using methods such as biometrics and secure protocols enables users to securely authenticate themselves in their applications without having to enter passwords.
In business, this means employees can easily access their work. Without having to enter passwords and IT still maintains total control across every login. Luckily, there’s also a new shift in the use of blockchain, for example, through decentralized identity or self-sovereign identity. As an alternative to traditional authentication methods, it’s also gaining quite some attention.
That’s it! Everything to know about Two-Factor Authentication (2FA) in detail. Do you think there’s something else worth mentioning? Well, you can share your additional thoughts, opinions, recommendations, or even contribution questions (for FAQ Answers) in our comments section. Otherwise, if you’ll need more help, you can always Consult Us and we’ll sort you out.